This project will explore corruption.
From Wiki
"Corruption is a general concept describing any organized, interdependent system in which part of the system is either not performing duties it was originally intended to, or performing them in an improper way, to the detriment of the system's original purpose."
It is a general term and widely applicable, which makes it an interesting subject for further inquiry. My goal is to use the flexibility of the word to explore the nuances of political corruption and data corruption simultaniously. My initial concept is to take jpg encoded photos of various corrupt political figures and using a Hex editor, inject plaintext descriptions of their acts of corruption and the subsequent impact of those actions. Warning: the images linked below are intentionally corrupted, and may render unpredictably or not at all! If you encounter problems viewing with one browser/platform try a different one.
I find that Safari, or Preview have the most robust error correction and display the most visually pleasing images. To view the text of the photos I use will a Hex editor, however, you do not need one to view the text in the image files, you should be able to see it by opening the JPG in most text editors. To make the images I used Hex Fiend however there are numerous other editors available.
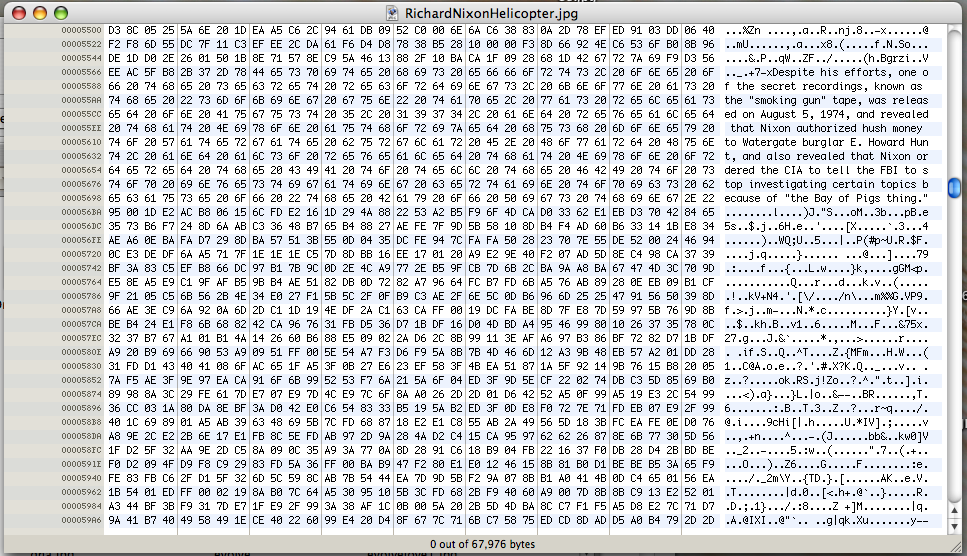
This is an example of how the Nixon photo looks when open in a hex editor.
Stego:
This project also has elements of steganography the process of concealing a message within another message. This an element of the project I would like to explore in depth. I just found these pages on audio stego in Aphex Twin songs and stego embeded within an images histogram The Aphex twin one is SUPER FREAKY
CO: Confirmed - Aphex Twin info is super freaky - you guys should check it out!
The Mysterious Changing Bitmap:













I have also started experimenting with ASCII injection into bitmap BMP images, because bitmap is a simpler, lossless format it is somewhat easier to modify and understand. I am able to specify parameters like pixel width/height and bit depth from the hex editor. One interesting point is that unlike JPGs which will vary in rendering from program to program but will always render the same within a program, the BMP files I have created will actually look different each time they are opened changing in unpredictable ways shifting both in colors and in pattern. This example may have to be downloaded and then opened (in preview) it is very small so cmd+ing is recommended.


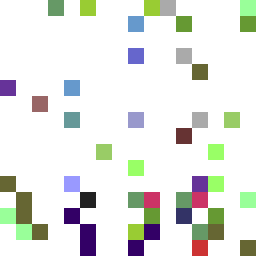
At this magnification it becomes appearant that a number of pixels stay constant.
CO: I want to know more about these three images and how they compare - they are different magnifications?
Ian's Rsponse: The images are all the same magnification (256 pixels from the 16px original) the first two show the change between each rendering of the image as it is reloaded, but at different speeds, in the last image I have removed all the pixels which change from reload to reload leaving only the 'constant' pixels which do not change. If you identify a pixel in the last image you can watch it in the other two where it will stay the same while everything else changes.
My theory is that the constant pixels are ones where my injected data falls within the bit depth that I defined for the image (8 bit, I think) while everything else falls outside that depth causing it to render differently depending on ???????. In other words if the image only has a color space to accommodate 10 colors as defined by digits 0-9 but I fed it a bunch of numbers between 0-99, some points would be in the 0-9 range and always render properly, but a 47 could turn into a 4 or a 7 depending on ???????. Again this doesn't really answer WHY it looks different every time, but it gives some insight into the how.
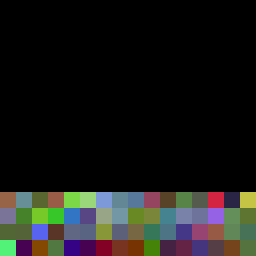 This is the same file as above except one hex pair, the one defining the number of bits per pixel, which is the color depth of the image has been changed. In the original file it was defined as 08 (08 in decimal) in this file it is 20 (32 in decimal) the amount of pixels in reduced to a quarter of what is was before which seems right if the number of bits to define a pixel was doubled twice. Most importantly this file renders the same way consistantly. The ??? may be that the color values of bmp files are stored in unsigned integers <---- look at the nice tables (is 11111111 -127 or 255???)
This is the same file as above except one hex pair, the one defining the number of bits per pixel, which is the color depth of the image has been changed. In the original file it was defined as 08 (08 in decimal) in this file it is 20 (32 in decimal) the amount of pixels in reduced to a quarter of what is was before which seems right if the number of bits to define a pixel was doubled twice. Most importantly this file renders the same way consistantly. The ??? may be that the color values of bmp files are stored in unsigned integers <---- look at the nice tables (is 11111111 -127 or 255???)
Notes:
I need to develop a better understanding of the jpeg jfif encoding format, specifically, to be able to create a jpg 'shell' which can then have arbitrary data inserted into it, and an understanding of how to declare the byte size of an image so that the injected data is displayed in full without being truncated.
There are two valuable sites which I have found that provide web based image corruption.
CORRUPT Corrupts images uploaded from the users computer
Glitch Browser Corrupts images in displaying a page from an arbitrary user defined URL
These are useful resources for quickly testing how an image degrades, however because my focus on politicians will emphasize willful concious corruption they are unsuitable because of their completely random methods of bit replacement and deletion.
Input:
I am very interested in other people reactions and suggestions about this project. You are encouraged to leave feedback in the comments section of this page or by email at metaphorever at gmail dot com. I am especially looking for suggestion of well documented cases of corruption and further suggestions on how the term can be applied to other instances of decay, information loss, entropy, and intentionally inappropriate action.
Colleen says: Look at Charles Fairbanks http://photographicapparatus.net/ and Eduardo Kac (mutation) http://www.ekac.org/geninfo2.html
Ben sez...
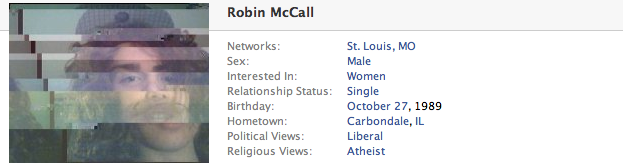
Thinking of a tangent you could go on with the language based images, you could do pixel portraits of people by formatting their name, date of birth, city of birth, current address, etc. This was an idea the stemmed off of someone asking if you had "done your name" yet. The love/hate language images were interesting, it might be another avenue to pursue.
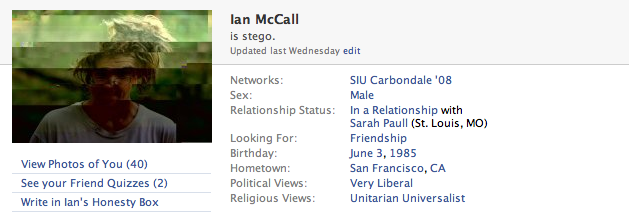
CO: What are planning to do here?
Response: I'm taking people profile pictures and encoding their profile information, Name, Sex, DOB, Relationship Status, etc and combining them. when the images are set as the user's profile picture you see the personal info that's stego'd into the photo displayed alongside the photo.
Comments (0)
You don't have permission to comment on this page.